2025 Cloud Security Outlook: Key Threats and Strategic Priorities
From core operations to innovation, the cloud underpins today’s digital business landscape. From running critical applications to enabling remote collaboration,...

In baseball, the Moneyball approach revolutionized how teams assess player performance. Instead of relying on traditional metrics like batting averages or home runs, Billy Beane and his team at the Oakland A’s shifted focus to more data-driven, nuanced statistics. This allowed them to spot undervalued players with skills that didn’t necessarily match conventional expectations but made a big impact on the game.
So, what if cybersecurity could take a page from this playbook?
What if we focused on data-driven, actionable insights to strengthen our defenses instead of relying on conventional security measures? Let’s explore how the Moneyball approach can be applied to cybersecurity and why it’s time to rethink the way we protect our digital assets.
From “Runs Scored” to “Threats Prevented”: A New Way of Measuring Success
In baseball, Moneyball introduced a new way to measure success – looking at the difference between runs scored and runs allowed rather than just counting wins.
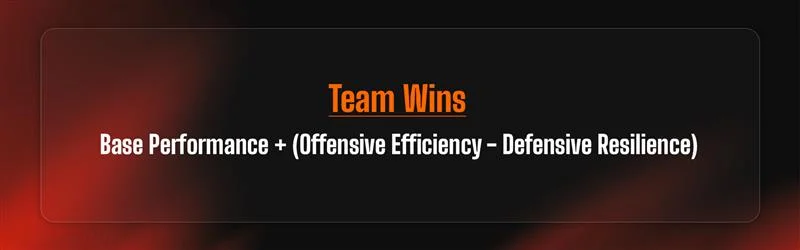
Base Performance + (On-Base Percentage + Slugging Percentage) – (Opponent’s On-Base Percentage + Opponent’s Slugging Percentage)
For better understanding, we can say
In cybersecurity, we can apply a similar concept by focusing on “Prevented Threats” (the attacks blocked successfully) and “Detected Vulnerabilities” (weaknesses identified in the system). Just as the A’s calculated their chances of making the playoffs by measuring run differences, cybersecurity teams can calculate their Security Posture Strength by evaluating how many threats were prevented versus how many vulnerabilities were detected.

A positive difference indicates a strong defense, much like a team that scores more than it allows. On the other hand, a negative or small difference shows gaps in the security infrastructure.
By shifting the focus from just detecting incidents to preventing them, organizations can build a proactive defense system, much like how Moneyball built a stronger, more efficient baseball team. This data-driven approach helps cybersecurity teams optimize resources and improve their overall security posture.
The Shift from Traditional Metrics to More Meaningful Ones
In baseball, traditional stats like batting average were once seen as the ultimate measure of a player’s value. However, Moneyball challenged this norm, introducing metrics like On-Base Percentage (OBP) and Slugging Percentage (SLG) that better reflected a player’s contribution to the team’s success.
Similarly, in cybersecurity, traditional metrics like the volume of detected threats or the number of vulnerabilities found don’t always tell the full story.

Metrics like Threat Containment Rate (TCR), Mean Time to Detect (MTTD), and False Positive Rate (FPR) are key indicators that provide a clearer picture of an organization’s cybersecurity performance. Just like OBP helped identify undervalued baseball players, these cybersecurity metrics highlight the true efficiency of a security system. They show how well threats are contained, how quickly vulnerabilities are detected, and how accurately alerts are raised, giving a much more accurate reflection of security strength.
Crucial Metrics for Measuring the efficiency of your security system
The Importance of Speed and Recovery
Another core component of the Moneyball strategy was looking beyond raw stats to determine a player’s impact on the game, focusing on those who could contribute quickly and effectively.
Similarly, in cybersecurity, metrics like Vulnerability Remediation Time (VRT) and Incident Recovery Time measure how fast an organization can address weaknesses and recover from attacks. Just as a baseball team needs to bounce back from losses, a cybersecurity system needs to quickly recover from incidents to minimize damage and prevent further exploitation.

This ability to recover quickly is as important as preventing threats in the first place, making it a key metric in any security strategy.
Moving Away from “Stacking Solutions” to Building a Converged Security System
Before the Moneyball approach, baseball teams often stacked players with different skills, hoping the combination would yield a winning performance. However, just like throwing together a bunch of talented players who don’t work well together doesn’t guarantee success, piling up individual security solutions often leads to inefficiencies.
Cybersecurity is not about having multiple tools; it’s about ensuring these tools work cohesively together to create a seamless defense.

Instead, the focus should be on building a converged security system, one that combines multiple functions into a single, cohesive tool. Much like a baseball team working together towards a common goal, a converged security system brings together threat prevention, detection, incident response, and recovery functions in a unified solution. This approach ensures that all parts of the security infrastructure work in harmony, making the entire system stronger and more effective against evolving cyber threats.
Conclusion: Rethinking the Playbook

When it comes to cybersecurity, it’s no longer about plugging leaks one by one. It’s about building a resilient system that anticipates and reacts before the storm hits. Just as Moneyball revolutionized baseball by focusing on the right metrics, cybersecurity needs to shift its focus to what matters: threat containment, recovery time, and the prevention-to-detection ratio. By paying attention to these factors, security teams can craft strategies that are not only efficient but also adaptable, ensuring all components – detection, prevention, recovery, and response – work in harmony to create a stronger defense.
This is where Argus, Genix Cyber’s flagship product, comes in. Argus is not just another security tool; it’s a complete strategy for managing and streamlining your organization’s security needs. Whether you’re working with a legacy security setup or a modern stack, Argus can snugly fit into your existing infrastructure, enhancing and bolstering your protection without the need for a complete overhaul. With its AI-driven insights, Argus doesn’t just defend against threats; it anticipates them and prevents them before they can cause damage. It offers a unified approach that improves security operations, reduces costs, and makes it an indispensable ally in the fight against evolving cyber threats.
From core operations to innovation, the cloud underpins today’s digital business landscape. From running critical applications to enabling remote collaboration,...
Cyber threats are advancing rapidly. Attackers are no longer just deploying malware. They are exploiting misconfigured cloud services, hijacking identities,...
The cloud has become the cornerstone of modern business. From running critical applications to enabling remote collaboration, cloud services now...
We’ll send you a nice letter once per week. No spam.
Copyright © 2025 Argus. All rights reserved.
Fill out the form below!