Secure every endpoint before threats break in
Argus helps you spot misconfigurations, detect threats in real-time, and maintain compliance across endpoints.
How Argus Secures Every Endpoint in Your Network
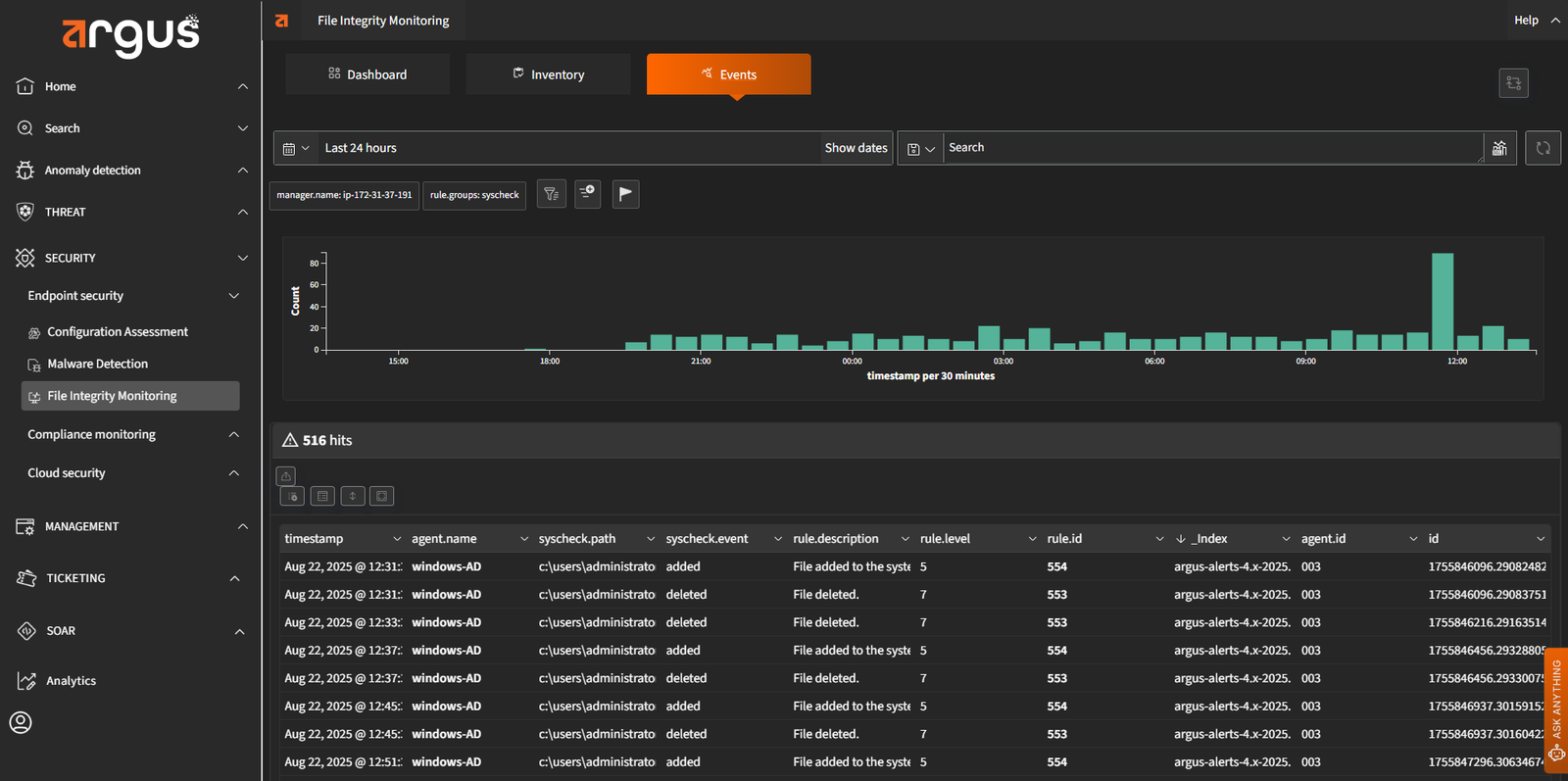
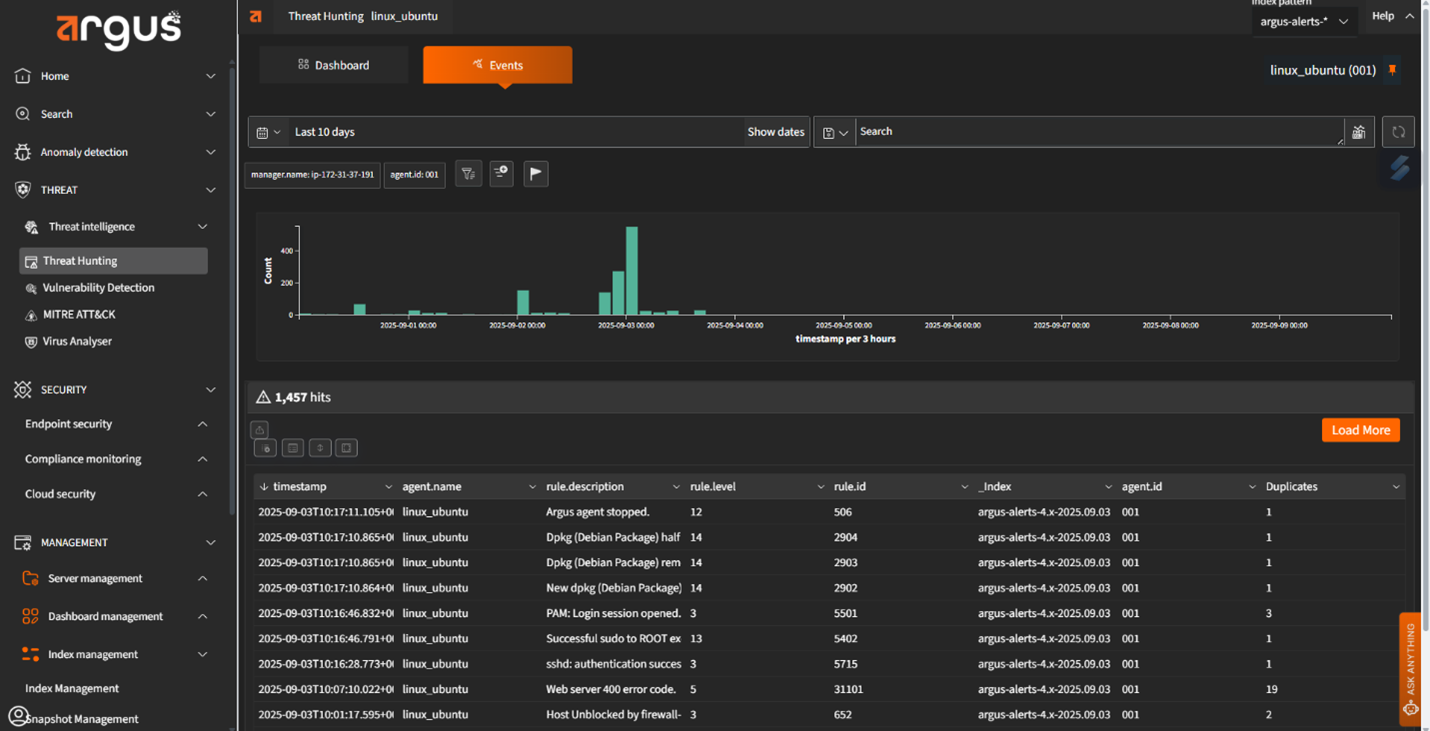
Live Threat Hunting and Forensics
Argus provides real-time visibility into every endpoint. It uses tools like OSQuery and Sysmon to uncover hidden anomalies, enabling immediate investigation and response. This level of visibility helps reduce the dwell time of advanced threats and supports detailed forensic analysis.
Adaptive Security Posture
Argus learns from past endpoint behaviors to dynamically adjust defenses. It adapts to new attack methods by using behavioral analytics and ensures that your endpoint security remains strong, even as threats evolve.
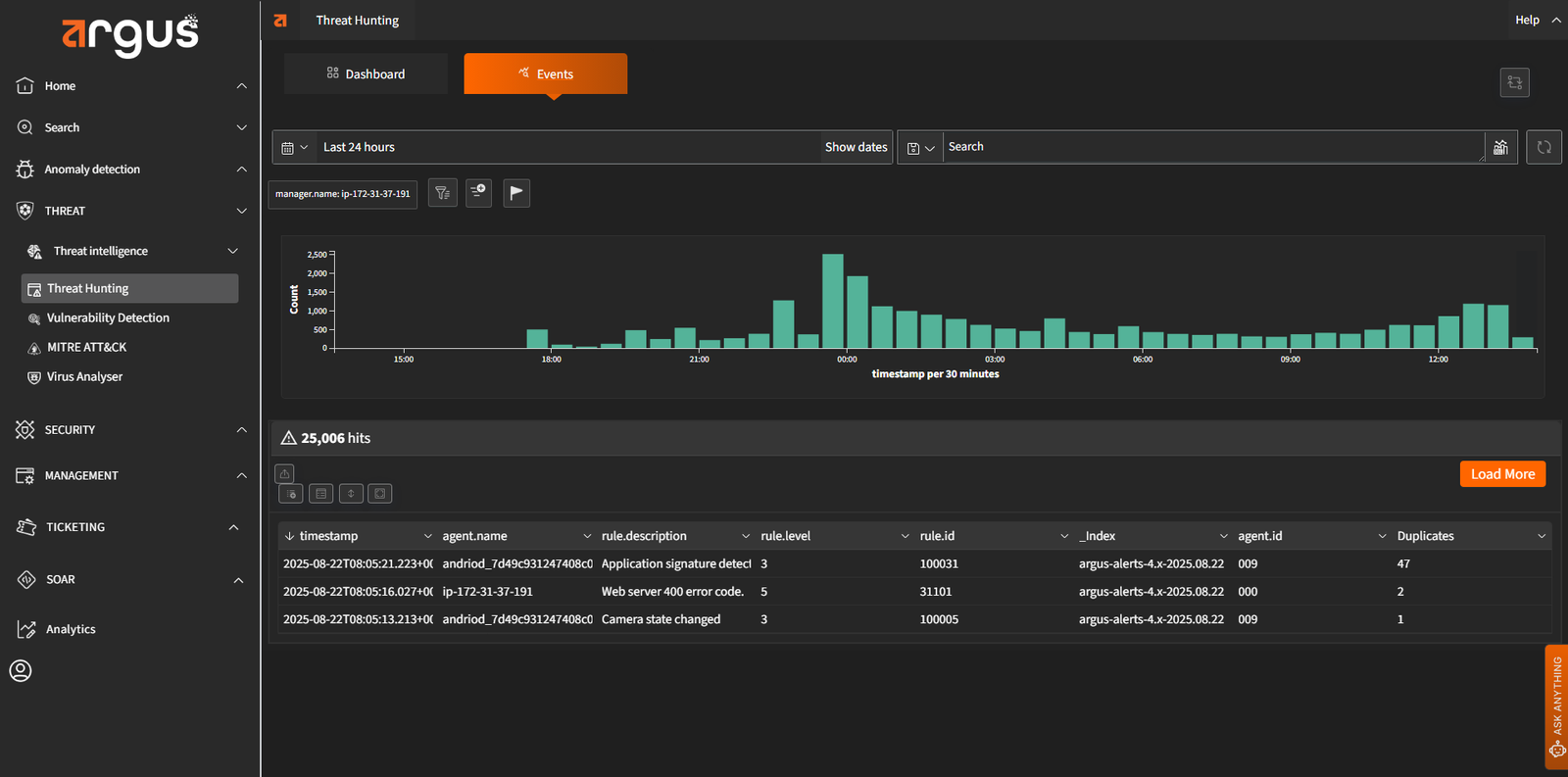
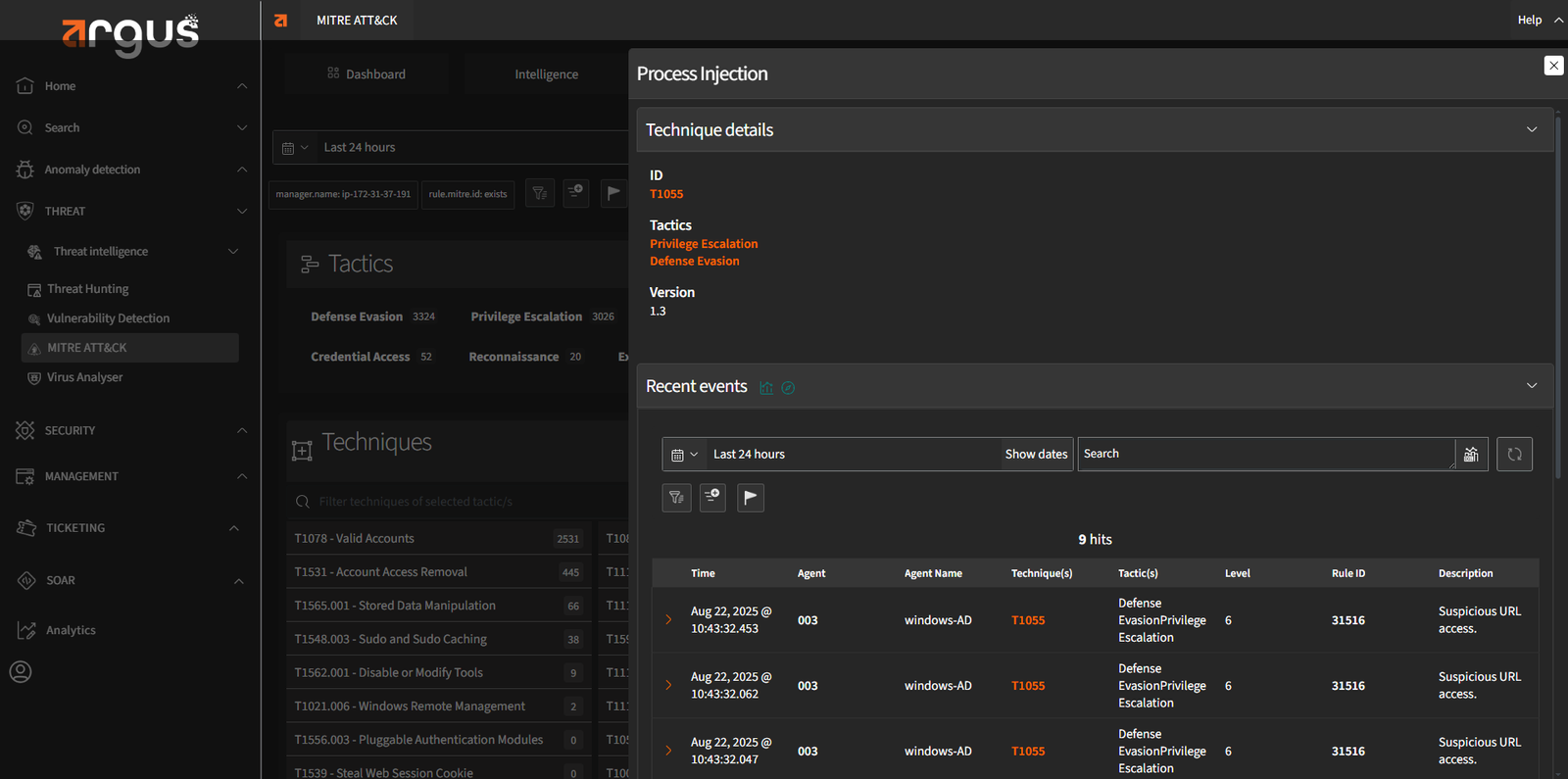
Operational In Intelligent Deception Technology sight
By planting strategic decoys and traps within your environment, Argus actively deceives attackers. This approach confuses threat actors and reveals their techniques, providing early warnings and opportunities to study their behavior in a controlled way.
See Argus in Action
Smart End Point Protection That Adapts to Every Threat

Real-Time Threat Detection on Endpoints Using OSQuery

How Deception Traps Disrupt Attack Paths

Forensic Analysis with Sysmon Data in Argus
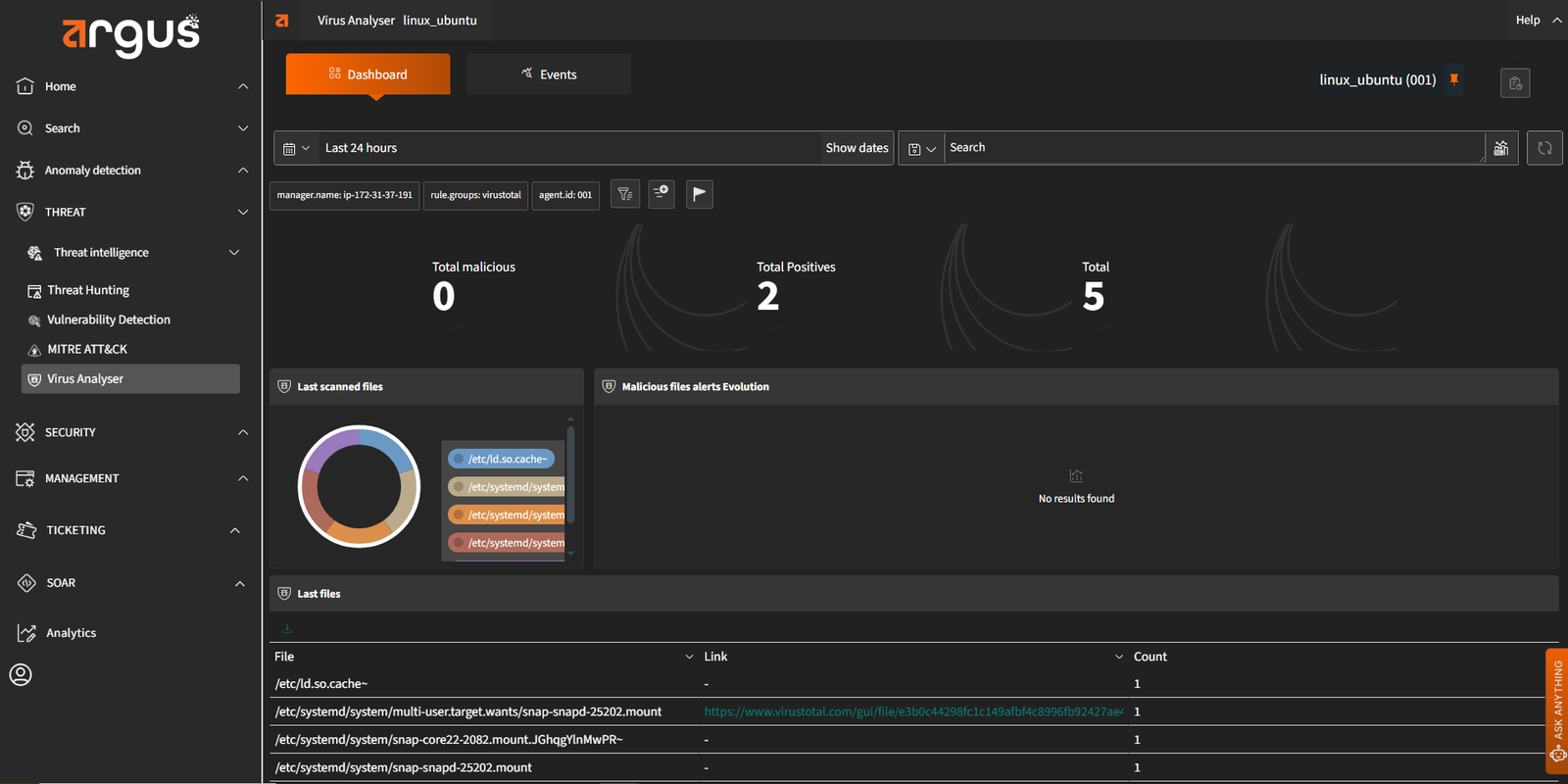
Deep Endpoint Visibility
Argus gives your team granular control and insights into all connected devices. From file activity and registry changes to user behaviors, everything is tracked and analyzed to identify unusual patterns early.
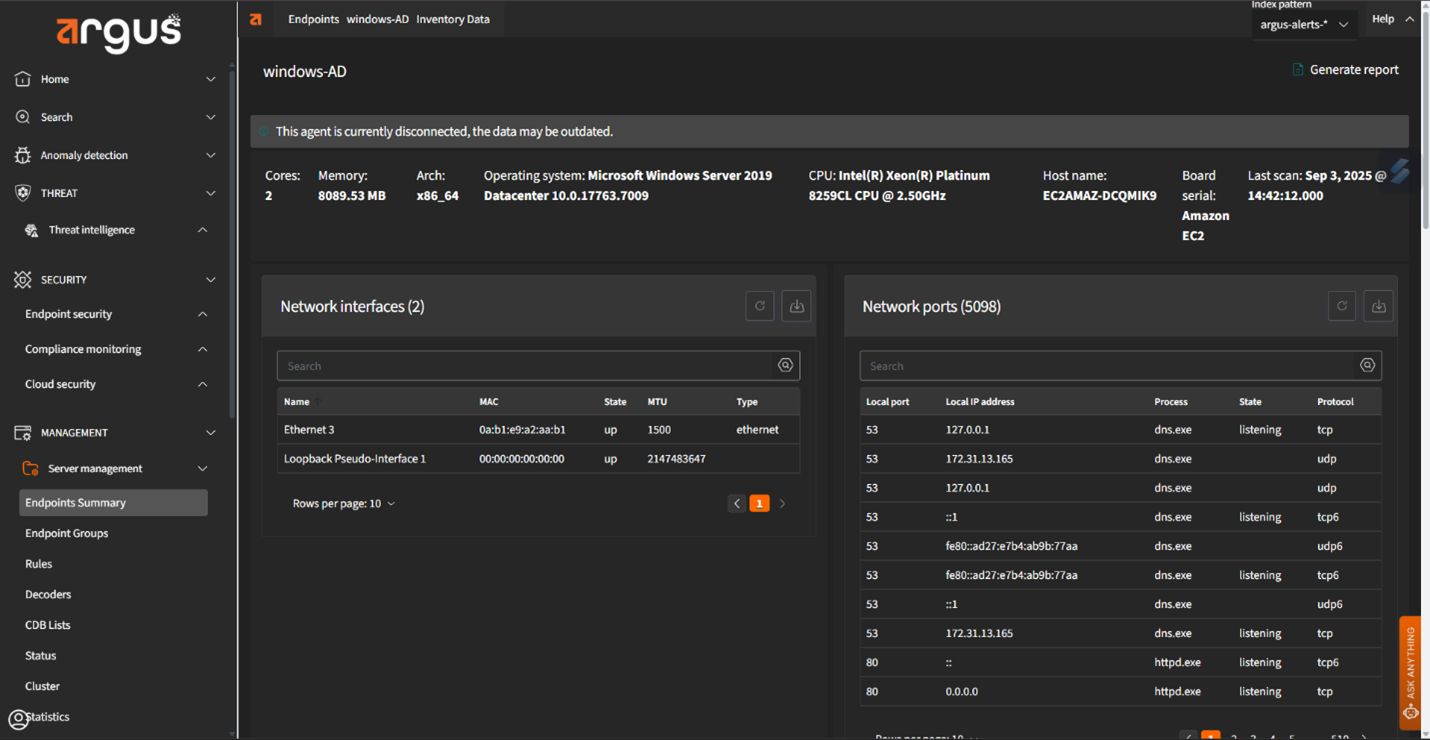
Automated Threat Containment
When a threat is identified, Argus can isolate compromised endpoints instantly. This action prevents the threat from spreading while giving your team time to investigate and remediate without disruption to business operations.
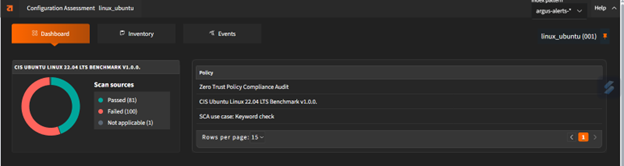
Custom Policy Enforcement
Enforce organization-wide security policies at the endpoint level. Argus allows you to create and deploy custom rules to control access, manage applications, and ensure devices meet security standards before connecting to your environment.
Integrated Deception Framework
Unlike static traps, Argus’ deception tactics are dynamic and intelligent. It mirrors real assets and adapts to network conditions, making it harder for attackers to distinguish fake from real. This helps detect lateral movement and insider threats with greater precision.
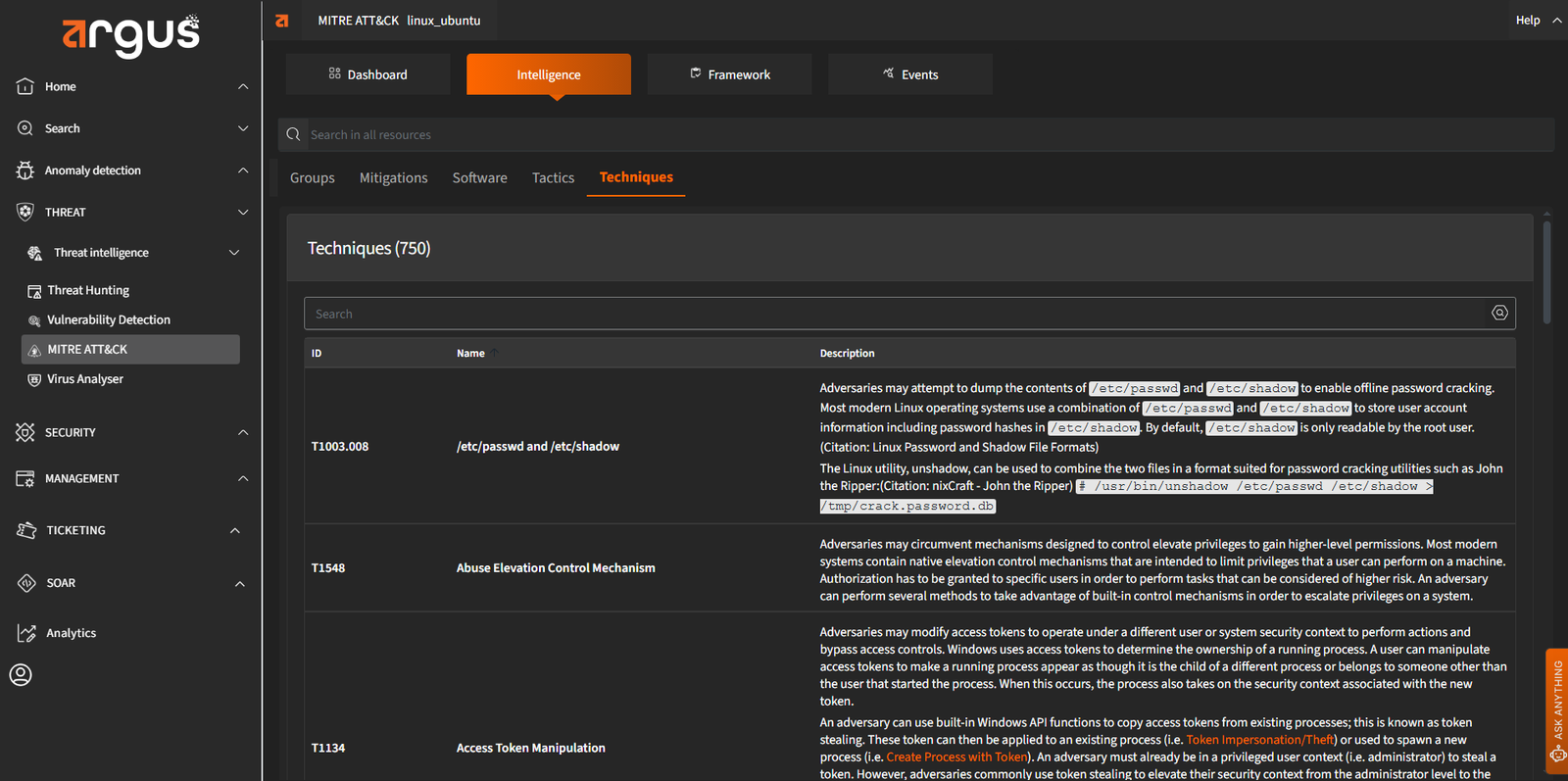
Why Argus for Endpoint Protection
Argus stands out by combining UEBA, intelligent deception, and forensic-grade monitoring in one powerful platform. Here’s what makes it the right choice:
Beyond Antivirus
Traditional tools only react. Argus proactively hunts, deceives, and isolates threats before damage is done.
Intelligence at the Edge
With real-time behavioral insights, Argus turns every endpoint into a source of threat intelligence.
Built for Scale
Whether you manage 100 devices or 10,000, Argus ensures consistent protection and visibility across your entire ecosystem.
File Integrity Monitoring
Bruteforce Attack

Trusted
Start Protecting Your Endpoints with Argus
Join the Next Generation of Endpoint Defense
Discover how Argus protects your endpoints with proactive intelligence and layered defenses. Start your free trial today and explore the power of deception, real-time visibility, and automated containment.

